Whilst we lack a formal, universally accepted definition of an algorithm, it is understood to mean the sequence of steps prescribed to carry out a task. The word 'algorithm' therefore includes everything from Google's search results display algorithm to IKEA furniture assembly instructions. This flexibility in definition is an advantage as it allows it to be used as a catch-all familiar term for the steps for calculations, data processing and automated reasoning. Almost all code can be broken down into algorithmic components - often one per function/subroutine/method.
To be more specific, an algorithm can be described as follows:
- requirements for an initial state from which the algorithm can begin executing
- requirements for initial input
- a finite series of well-defined instructions
- an end state where the algorithm terminates, possibly with output
The above could be described as an abstracted algorithm for algorithms itself.
One informal definition of an algorithm is that it is a "set of rules which precisely defines a sequence of operations"1 which actually defines all computer programs, mathematical and otherwise. In this respect, algorithms can be said to be the way computers turn data into meaningful, useful actions.
There are many forms of notation and language that can express algorithms. Day-to-day instructions are transmitted between people in natural language, such as a parent teaching a child how to tie their shoes, or an adult following tech support instructions over the phone. In a more computer-orientated setting, algorithms meant to be implemented as code are most often expressed in pseudocode or flowcharts for improved clarity, while algorithms that have already been implemented are written in a programming language or control table.
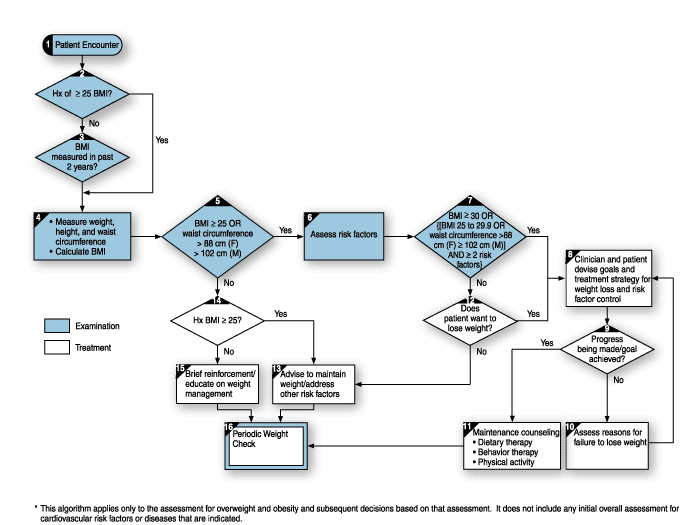
This medical algorithm, expressed as a flowchart, is meant for a human to follow, but by breaking it into steps, one can see how one might begin to automate it.
References:
1. Stone 1973:4
Icon credit AlMare
© BrainMass Inc. brainmass.com June 29, 2024, 9:11 pm ad1c9bdddf