Program execution has nothing to do with cancellation or termination. All programs are essentially sets of instructions for a computer to carry out, and that act of carrying them out is known as execution. Each instruction may cause a number of actions to be taken by the processing machine, with effects that can affect any number of components of that computer, depending on how the instructions were written. The systems that do the executing for a machine are known as interpreters as they read the code in and follow its instructions. A human typing commands into a terminal is an example of an interpreter in action, interfacing between the human input and the processor, but programs may also execute in batch processes without any human interaction necessary. Interpreters can be held in contrast to compilers which perform a translation of the code a programmer writes into a more low-level language that can be directly executed by a processor much more simply and quickly than the original high-level sourcecode. The file produced by a compiler this way is often called the executable.
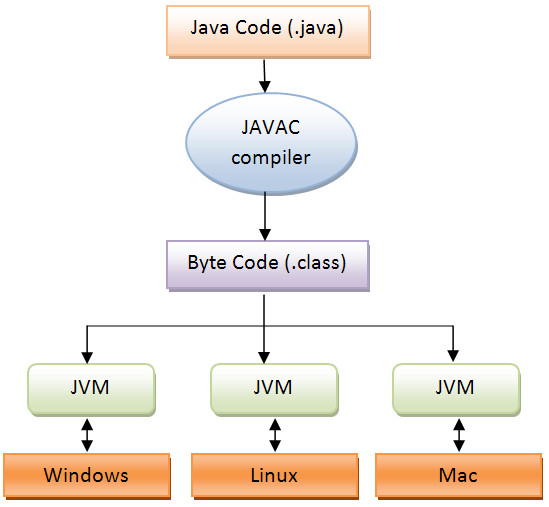
The compiling process to get an executable for 3 common OSes from a program written in Java. Image credit Loboh.
As only a few types of programs are executable on a bare machine, most programs are designed with assumptions, both implicit and explicit, about the resources available for execution. The presence of an operating system is almost always a safe bet, and most programs do rely on the support of such a system at the very least. Run-time libraries specific to the language the program is written in are another thing programs tend to rely on access to which are not supplied by the computer from factory settings.
© BrainMass Inc. brainmass.com July 24, 2024, 12:54 pm ad1c9bdddf