An important part of security is being able to verify the identities of people or programs attempting to access your data. Some of them, you will want to allow access, of course, but allowing someone with malicious intentions could have devastating effects. Another kind of authentication one might need to perform is confirming the validity of a piece of software as originating and functioning like it claims. This includes tracing the creator of a program. All these kinds of authentication rely on identification of the object in question as something expected or legitimate.
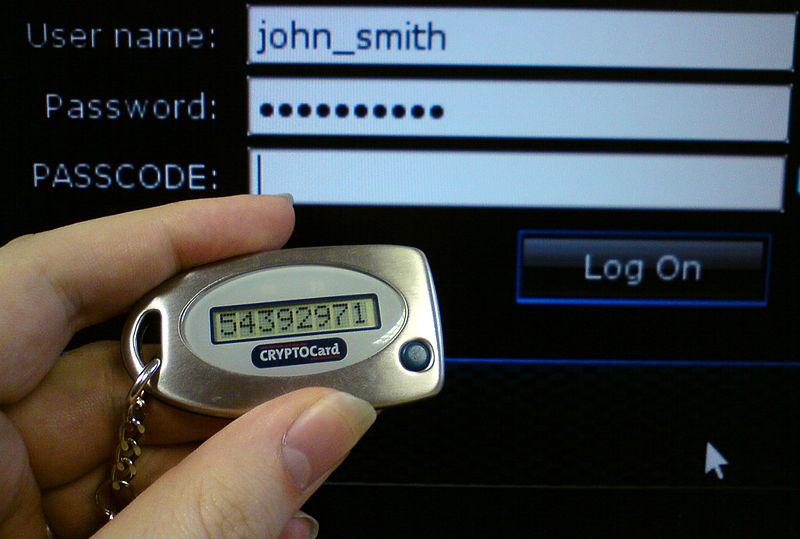
A security token for two-factor authentication [Photo credit Brianetta]
Three main ways of performing that authentication exist:
- Checking the offered form of identity for fraud or malpractice
- Comparing the specifications of the person or software attempting to gain access to what is known about others like them
- Using existing specifications or external documentation to check if the incomer is expected
Also, there exist three factors that can act as clues for the discerning program to judge the authenticity of an incoming third party:
- ownership - something the user/software has that can be verified, e.g. rank
- knowledge - something the user/software knows that can be verified, e.g. a password
- inheritance - something the user/software is or does that can be verified, e.g. if the object is part of a larger family that has been verified
Using these three factors and three techniques, one may authenticate anything with a reasonable degree of certainty.
© BrainMass Inc. brainmass.com June 30, 2024, 10:15 am ad1c9bdddf